Enterprise Mobility: Digging & Defying the Information Security Threats

Are you tired of feeling chained to your desk while running your business? What if we told you that you could access all your business applications and data from your mobile device, no matter where you are in the world? It sounds like a dream come true, and with the rise of enterprise mobility, it’s becoming a reality. This groundbreaking technology is transforming the way businesses operate, but it’s not all sunshine and rainbows. The convenience of enterprise mobility has opened the door to a world of enterprise mobile security threats that businesses must face head-on.
From cyber attacks to data breaches, the risks are real, and the consequences can be devastating. According to a report by Verizon, 43% of all data breaches occur in the mobile environment. The consequences of a data breach can range from financial loss to reputational damage. As the CEO of IBM, Ginni Rometty, once said, “Cybercrime is the greatest threat to every company in the world.”
So, how can businesses reap the benefits of enterprise mobility while minimizing the risk of data breaches? In this blog, we’ll take a deep dive into the world of enterprise mobility, the information security threats it poses, and the solutions to overcome them. Are you ready to learn how to dig and defy the information security threats in the world of enterprise mobility? Let’s first get a glimpse of various security threats.
Information Security Threats In Enterprise Mobility
Alongside providing diverse benefits, enterprise mobility also runs the risk of getting affected by several security threats:
Mobile Threats
Malware and viruses
Mobile malware and viruses are a serious threat to enterprise mobility, as they can steal sensitive data, damage devices, and compromise security. According to MDP malware attacks are rising, especially on Android phones, which account for 72.2% of the total market share.
These attacks can be triggered by downloading rogue apps, clicking on malicious links or attachments, or connecting to unsecured Wi-Fi networks. To protect against malware and viruses, businesses need to implement mobile security solutions, conduct regular security audits, and educate employees on cybersecurity best practices.
Network-based attacks
Network-based attacks occur when cybercriminals exploit vulnerabilities in the network infrastructure to intercept and manipulate mobile network traffic.
Attacks in this category can include Man-in-the-Middle (MitM) attacks, where cybercriminals intercept communications between two parties to steal sensitive data or modify it for their own purposes. Such attacks can be carried out on unencrypted or poorly secured networks, making them a significant threat to mobile users.
Device loss or theft
One of the biggest threats to information security in enterprise mobility is the loss or theft of mobile devices. When an employee loses their device or it is stolen, sensitive data can be exposed, leading to potential financial losses for the organization.
To prevent data loss or theft, organizations should implement security protocols such as device encryption and remote wipe. Being proactive in securing mobile devices can help protect against this significant threat to information security.
Rogue apps
Rogue apps can be a serious problem for companies that rely on enterprise mobility. These apps are designed to steal data or infect devices with malware, and can often be hard to spot as they appear to be legitimate apps.
To protect against these threats, organizations need to have clear policies in place regarding app installations and ensure that employees are trained on how to identify and avoid rogue apps. By taking these steps, companies can mitigate the risks of data breaches and keep their sensitive information secure.
Phishing attacks
Phishing attacks are a common information security threat in enterprise mobility. One example of a company that faced a phishing attack is Twitter. In July 2020, Twitter experienced a massive breach in which hackers gained access to high-profile accounts and used them to promote a Bitcoin scam.
The breach was a result of a successful phishing attack that targeted Twitter employees through a social engineering campaign. This incident highlights the importance of implementing strong security measures, such as two-factor authentication and employee training, to prevent phishing attacks from compromising sensitive data.
Unsecured Wi-Fi
Unsecured Wi-Fi connections are a major concern in enterprise mobility as they can be exploited by cybercriminals to access sensitive data on mobile devices. For instance, a hacker could create a fake Wi-Fi network with a similar name to a legitimate network, tricking users into connecting to it and granting access to their confidential information.
A live example is the Starbucks Wi-Fi hack in 2018, where cybercriminals installed malware on the company’s Wi-Fi network, compromising customers’ personal information, credit card details, and login credentials.
General threats
Insider threats
These threats arise from trusted individuals with authorized access to an organization’s systems or data. They can be employees, contractors, or partners who intentionally or inadvertently pose risks to security. Insider threats can result in data breaches, intellectual property theft, or sabotage.
Organizations must be vigilant in implementing access controls, monitoring user activities, and providing comprehensive cybersecurity training to mitigate these risks and protect sensitive information.
Social engineering attacks
Social engineering attacks are cunning attempts by hackers to manipulate people into revealing confidential information or taking certain actions. This type of attack relies on psychological manipulation rather than technical skills.
As security expert Kevin Mitnick puts it, “What I found personally to be true was that it was much easier to manipulate people than it was to hack into their systems.” Social engineering attacks can take various forms, such as phishing emails, phone calls, or text messages, and they can be hard to detect because they often appear legitimate.
Third-party risks
Third-party risks in enterprise mobility highlight the potential vulnerabilities introduced when relying on external vendors or suppliers. As renowned security expert Bruce Schneier stated, “If you outsource your security to a third party, you’re outsourcing your security.”
By entrusting sensitive data and access to third parties, organizations expose themselves to the risk of a security breach. It is crucial to thoroughly assess the security measures and practices of third-party vendors to mitigate these risks.
Cloud security risks
With the increasing adoption of cloud-based solutions, organizations face new security challenges. Cloud security risks refer to the risks associated with storing data in cloud environments. These risks can be in the form of data breaches, insider threats, or insecure APIs.
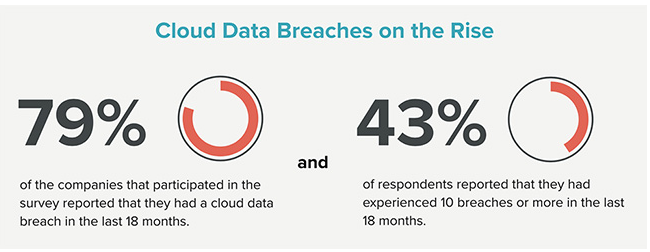
Image source:- helpnetsecurity.com
Data breaches and leaks
Data breaches and leaks pose a significant threat to enterprise mobility, which refers to the trend of employees using mobile devices to access the organization’s data and perform work tasks. As mobile devices become more integrated into work processes, the risk of sensitive data being accessed or stolen through a security breach increases.
A data breach can result in the loss of customer data, intellectual property, and financial information, leading to severe consequences for an organization’s reputation and bottom line.
Cyber espionage and hacktivism
Cyber espionage and hacktivism are two menacing forms of cyber threats that have gained notoriety in recent years.
Cyber espionage involves sophisticated attacks by nation-state actors aimed at stealing valuable data, intellectual property, or confidential information, while hacktivism is often politically motivated and involves online activism through malicious activities like website defacement and denial-of-service attacks.
Both types of attacks pose serious risks to businesses and organizations, as they can cause significant damage to reputation, operations, and financial stability.
How to Deal With Information Security Threats
Dealing with information security threats requires a proactive and comprehensive approach. Here are some strategies and measures that organizations can take to address these threats:
Navigate the Hazards
Protecting your workplace mobility environment necessitates a proactive risk management strategy. You can gain a full picture of the exclusive security challenges you face by identifying potential flaws and prioritizing key assets. With this insight, you can create a strategic risk assessment plan to mitigate potential risks and defend your organization’s valuable data and systems.
Layer Up Your Security
Adopt a multi-layered security approach to provide defense-in-depth. This involves implementing threats for enterprise application security measures at various levels, including network security, device security, and data security. Use firewalls, intrusion detection systems, encryption, secure coding practices, and access controls to protect your mobile infrastructure.
Time to Protect Your Enterprise
Create a rock-solid foundation for your enterprise mobility security by establishing robust policies and procedures. Build comprehensive guidelines covering everything from acceptable usage and password management to device and data management, and incident response. Keep these policies updated regularly to stay ahead of evolving security threats and ensure your organization is always protected.
Secure Business from Inside Out
Protecting your business from security breaches starts with securing it from the inside out. Unfortunately, human error is a common culprit behind data leaks and hacks. So, it’s crucial to arm your employees with the knowledge and skills to prevent such mishaps.
Educating them on information security best practices, such as recognizing phishing attacks, practicing safe browsing habits, and using strong passwords, is a must. Furthermore, encouraging device encryption and establishing a culture of reporting suspicious activities promptly can help avoid disasters.
Patch to Protect
Keep all mobile devices, applications, and systems up to date with the latest security patches and updates. Regularly check for vulnerabilities and apply patches promptly to mitigate potential risks. This includes not only the operating systems but also mobile apps and third-party software used within your organization.
Stay Alert, Stay Secure
Stay one step ahead of cybercriminals by implementing advanced security monitoring tools and techniques. Network monitoring, log analysis, and security information and event management (SIEM) systems can help you detect and respond to security incidents in real time. But don’t stop there! Regularly reviewing logs and analyzing security events can help you spot unauthorized access or malicious activities before they can cause serious harm.
Secure with Audits
Don’t wait for a security breach to happen before you take action. Be proactive and conduct regular security audits and assessments to ensure that your security measures are effective. Get the help of third-party security experts to perform penetration testing, vulnerability assessments, and security audits to identify any weaknesses or gaps in your security posture. By doing so, you can stay ahead of potential threats and prevent any unauthorized access or malicious activities. It also shows that you take security seriously and are committed to protecting your business and customers’ sensitive information.
Ready for Action
Develop a well-defined incident response plan to guide your organization in handling security incidents effectively. This plan should include steps for containment, investigation, mitigation, and recovery. Regularly test and update the plan to ensure its effectiveness.
By adopting these strategies and measures, organizations can better protect their enterprise mobility environments and mitigate the risks posed by information security threats. It is an ongoing process that requires continuous monitoring, updating, and improvement to stay ahead of evolving threats.
The Final Words
In today’s digital era, where mobility has become an integral part of our lives, it’s essential for businesses to understand and address the potential security threats posed by enterprise mobility. As discussed earlier, conducting a risk assessment and implementing strong security policies and procedures are critical steps in safeguarding your organization’s valuable assets.
We at Finoit Technologies , a reliable enterprise application development company in the USA, understand the importance of data confidentiality, and we strive to provide our clients with the best security measures for the mobile applications we develop. Our team of experts assesses and implements necessary security measures throughout the development life-cycle to ensure that our clients’ apps are safe and secure. If you’re looking for a reliable tech partner to develop your mobile app idea, feel free to approach us at info@finoit.com. We’ll be happy to assist you.

